I started experimenting with Tailscale (along with the self-hosted coordination server Headscale) and I like it pretty much. One of the interesting properties of Tailscale is the separation of control and data plane, where it tries to establish a direct point-to-point WireGuard tunnel between peers. It gracefully falls back to relay servers if such a connection is not possible. This avoids a central VPN server that needs to be involved in every connection.
One can use the command tailscale status to find out if a direct
connection between peers is used:
100.64.0.1 host1 net1 linux active; relay "lhr", tx 33036 rx 27232
100.64.0.2 host2 net2 linux active; direct 192.168.1.2:41641, tx 13892 rx 10024
The connection to host1 is relayed via a DERP server and the
connection to host2 is direct where the WireGuard tunnel uses
192.168.1.2 as the outer IP address.
One day, I noticed something odd: direct connections between two peers in my local network are only possible if one of them uses WLAN. As soon as both peers are connected to the same switch, packets are sent via a relay. The peers are all on the same LAN and there are no weird firewall rules that block traffic. So it clearly should use a direct connection.
The solution is buried in the config of my HP ProCurve switch. It tries
to be smart about DoS protection and has the innocent looking flag
Auto DoS set:
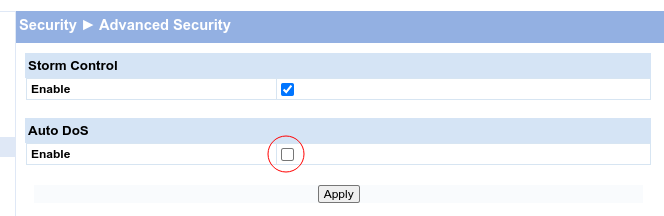
A direct connection is possible as soon as the feature Auto DoS is disabled.